Researchers at Oligo Security have uncovered a critical, 18-year-old vulnerability dubbed “0.0.0.0 Day” that poses a severe threat to all major web browsers, including Chrome, Firefox, and Safari. This flaw allows malicious websites to circumvent robust browser security measures and directly interact with services operating on a local network. The potential consequences are dire, including unauthorized access, data breaches, and even remote code execution.
How Does It Work?
The root of the problem lies in the inconsistent implementation of security mechanisms across different browsers and a general lack of standardization within the industry. The seemingly innocuous IP address, 0.0.0.0, often used as a placeholder, has been exploited to grant attackers access to local services, ranging from development tools to core operating system components.
By leveraging this vulnerability, malicious actors can:
- Bypass browser security: Circumventing safeguards designed to protect users.
- Access local services: Gain unauthorized entry to applications and systems on the same network.
- Steal data: Exfiltrate sensitive information from compromised devices.
- Execute malicious code: Take complete control of affected systems.
The use of the 0.0.0.0 Day vulnerability allows attackers to port scan users, potentially leading to the identification of open ports and vulnerable services.
Google’s introduction of Private Network Access (PNA) aims to extend CORS by restricting websites’ ability to send requests to servers on private networks. PNA proposes distinguishing between public, private, and local networks, preventing requests from being sent to more secure contexts.
According to the current PNA specification, the following IP segments are considered private or local:
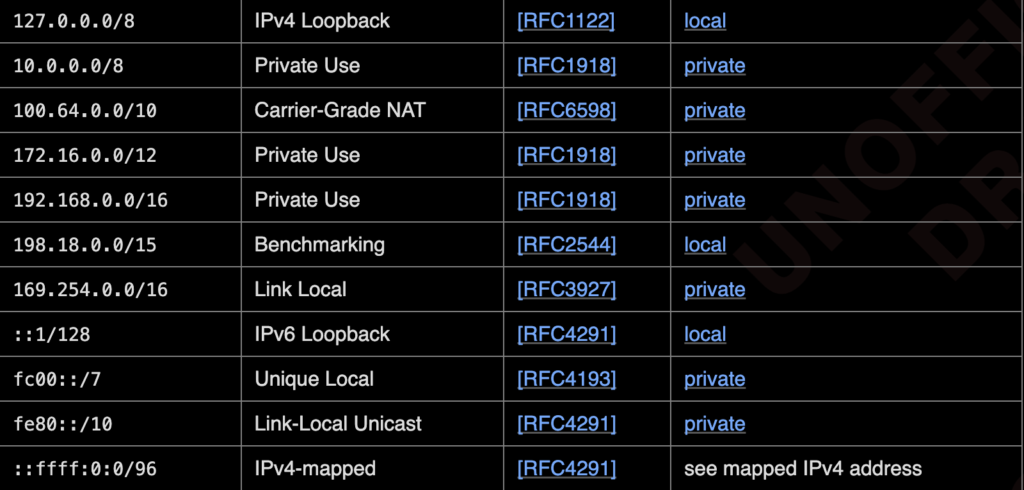
Putting 0.0.0.0 To the Test: PNA Bypass
A Longstanding Issue
A bug report dating back to 2006 highlights the persistent nature of this problem. Despite numerous attempts to address it, the issue has remained unresolved until now. The lack of industry-wide standards for browser security has created an environment ripe for exploitation.
Impact and Mitigation
The implications of the 0.0.0.0 Day vulnerability are far-reaching, affecting both individuals and organizations. While the risk is heightened for users running macOS and Linux (Windows systems are less vulnerable due to OS-level protections), everyone is at risk.
To mitigate the threat, browser vendors are actively working on patches and updates. Google Chrome and Chromium-based browsers are leading the charge with the implementation of Private Network Access (PNA), a feature designed to restrict website access to private networks. However, full protection will require time.
Following responsible disclosure, browser vendors have acknowledged the security flaw and are working to implement browser-level mitigations.
Google Chrome (and Chromium-based browsers like Edge)
- PNA Initiative: Evolving Private Network Access (PNA) led by Google.
- Vulnerability: 0.0.0.0 bypasses PNA, allowing access to private IPs.
- Fix Rollout: Blocking 0.0.0.0 from Chrome 128, fully effective by Chrome 133.
- Statistics: 0.015% of websites (around 100K) communicate with 0.0.0.0.
Apple Safari
- WebKit Changes: Now blocks 0.0.0.0 access.
- Implementation: Requests to all-zero IP addresses are blocked.
Mozilla Firefox
- Current Status: No immediate fix; PNA not initially implemented.
- Specification Update: Fetch specification updated to block 0.0.0.0.
- Future Plans: Implementation of PNA will eventually block 0.0.0.0.
A Call for Industry Collaboration
The discovery of the 0.0.0.0 Day vulnerability underscores the urgent need for greater collaboration among browser developers. Establishing standardized security protocols and practices is essential to prevent similar vulnerabilities from emerging in the future.
Until robust security measures are fully implemented, users are advised to exercise caution when browsing the web and avoid clicking on suspicious links or downloading files from unknown sources.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. Summitsystemsissp assumes no liability for the accuracy or consequences of using this information.







