A new ransomware threat appeared on the scene in February 2024: Ransomhub, a RaaS offering advertised on cybercrime forums.
A recent ransomware attack by the Ransomhub group on a Spanish bioenergy plant underscores the escalating risk of cyberattacks targeting Industrial Control Systems (ICS). According to a report by Cyble Research & Intelligence Labs (CRIL), the attack specifically targeted the plant’s Supervisory Control and Data Acquisition (SCADA) system, a critical component for managing operations.
Ransomhub’s strategy involves not only encrypting data but also disrupting essential functions by gaining access to SCADA systems. This was evident in the recent attack, where they claimed to have encrypted over 400 GB of data while maintaining control over the plant’s SCADA systems. This highlights the group’s ability to cause significant disruption beyond data loss.
Ransomhub’s Rise and Evolving Tactics:
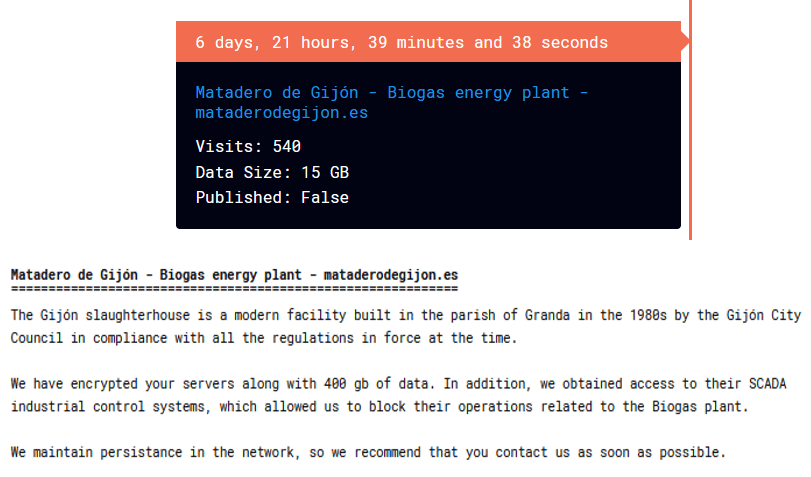
Ransomhub posts on their DLS.(Source: Cyble)
Emerging in February 2024 as a Ransomware-as-a-Service (RaaS) on cybercrime forums, Ransomhub initially targeted the IT and ITES sector, primarily in the United States. However, their recent attack on a bioenergy plant and focus on SCADA vulnerabilities indicate a strategic shift towards Operational Technology (OT) environments. This aligns with a broader trend in the ransomware landscape where attackers exploit interconnected systems for maximum impact.
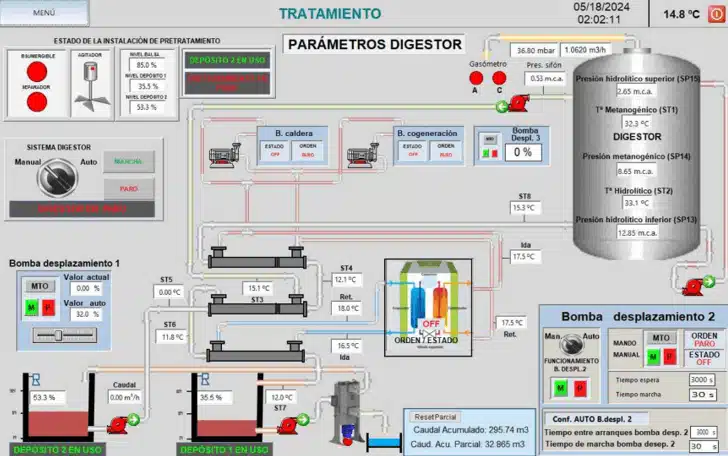
Alleged SCADA control of Gijón Bio-Energy Plant Digestor Tank (Source: Cyble)
Heightened Vigilance Needed:
CRIL’s investigation reveals a concerning link between Ransomhub and Initial Access Brokers (IABs) operating on Russian-language forums. This suggests a sophisticated network for acquiring access to victim networks. This alliance underscores the urgent need for organizations to be more vigilant and implement proactive defense measures to identify and prevent potential breaches.
Bolstering Defenses: Protecting Industrial Control Systems (ICS) from Ransomware
The recent surge in ransomware attacks, exemplified by Ransomhub’s assault on Industrial Control Systems (ICS), underscores the urgent need for organizations to bolster their cybersecurity defenses. Here are key recommendations to fortify your ICS environment:
Limiting Attack Surface:
Network Segmentation: Implement robust network segmentation to isolate critical ICS components from non-essential systems. This minimizes the attack surface and hinders attackers’ ability to move laterally within your network.
Patch Management: Prioritize regular software updates and patch management protocols to address known vulnerabilities that could be exploited by ransomware.
Early Detection and Response:
Secure Remote Access: Utilize secure remote access methods like Virtual Private Networks (VPNs) with strong authentication measures. This minimizes the risk associated with unauthorized access attempts.
Network Monitoring: Diligently monitor network logs for suspicious activity. Early detection of anomalies can prevent a full-blown ransomware attack.
Enhanced Security Posture:
Asset Management: Maintain detailed inventories of your OT/IT assets. This facilitates vulnerability assessments and ensures all critical systems are addressed in your security protocols.
Continuous Monitoring: Deploy continuous monitoring solutions to proactively identify and address potential security issues within your ICS environment.
Preparedness is Key:
Incident Response Planning: Develop and regularly test incident response plans. This enables a swift and coordinated response to minimize downtime and data loss in the event of a ransomware attack.
By implementing these proactive measures, organizations can significantly bolster their defenses and mitigate the growing threat of ransomware attacks against their critical ICS infrastructure. The recent incident serves as a stark reminder of the escalating risks. Heightened awareness and proactive security posture are essential to safeguard your ICS from online cyber threats.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. Summitsystemsissp assumes no liability for the accuracy or consequences of using this information.







