
For over two years, malicious actors have been exploiting unpatched Microsoft Exchange Servers to deploy keylogger malware in targeted attacks.
These attacks primarily focus on entities in Africa and the Middle East, according to a recent report by Positive Technologies, a cybersecurity firm based in Russia.
The report details how attackers leverage known vulnerabilities collectively referred to as “ProxyShell” (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207). These vulnerabilities, patched by Microsoft in May 2021, allow attackers to bypass authentication measures, escalate privileges, and ultimately execute malicious code remotely.
Positive Technologies identified over 30 victims, including government agencies, banks, IT companies, and educational institutions. The earliest compromise linked to this campaign dates back to 2021, highlighting the ongoing threat posed by unpatched systems.
The attacks follow a specific pattern. First, attackers exploit the ProxyShell vulnerabilities to gain access to the targeted Exchange Server. They then inject malicious code into the server’s main login page (“logon.aspx”) and add a hidden function (“clkLgn()”) designed to capture user credentials when they attempt to log in. These stolen credentials are then stored in a file accessible from the internet, allowing attackers to harvest them remotely.
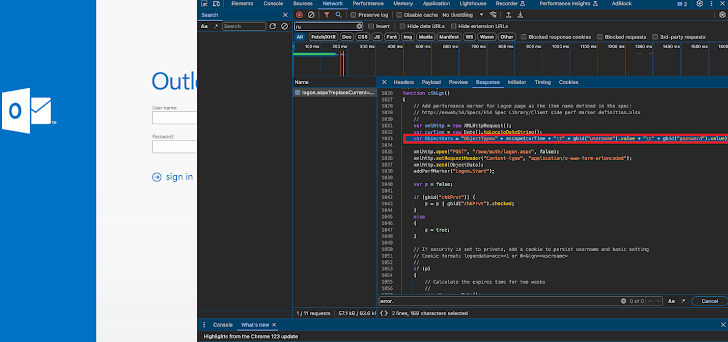
While the specific threat actor behind these attacks remains unknown, Positive Technologies urges organizations to prioritize patching their Microsoft Exchange Servers to the latest version. This is the most critical step in mitigating the risk of compromise.
For organizations that suspect their servers may already be compromised, Positive Technologies recommends inspecting the Exchange Server’s main login page for the presence of the “clkLgn()” function. Additionally, they advise checking the “logon.aspx” file for the path to a hidden file where stolen credentials might be stored. If a compromise is confirmed, organizations should immediately change compromised account credentials, delete the stolen credential file, and consider seeking assistance from cybersecurity professionals for remediation.
https://thehackernews.com/2024/05/ms-exchange-server-flaws-exploited-to.html
Credit images: Microsoft and Automation.com







